 A continuation of “audio networking overview” in last year’s edition of source material. The merging of the AV and IT world is observably becoming more standardised across multiple industries, the application of which can sometimes seem overwhelming and therefore, in my opinion, underutilized. Existing IT networks may be the key transport method for a lot of broadcasters & AV users. In contrast, many IT users may have concerns about routing signals alongside existing data traffic, potentially unaware of the bandwidth capabilities and security options available to the consumer. Becoming ever more present in broadcast and AV applications, computer networking has and is continuing to change the way we transport media around the world. With the demand for control and communications, AV and IT specialists continue to develop more inventive ways to accommodate AV applications over an IT infrastructure.
A continuation of “audio networking overview” in last year’s edition of source material. The merging of the AV and IT world is observably becoming more standardised across multiple industries, the application of which can sometimes seem overwhelming and therefore, in my opinion, underutilized. Existing IT networks may be the key transport method for a lot of broadcasters & AV users. In contrast, many IT users may have concerns about routing signals alongside existing data traffic, potentially unaware of the bandwidth capabilities and security options available to the consumer. Becoming ever more present in broadcast and AV applications, computer networking has and is continuing to change the way we transport media around the world. With the demand for control and communications, AV and IT specialists continue to develop more inventive ways to accommodate AV applications over an IT infrastructure.
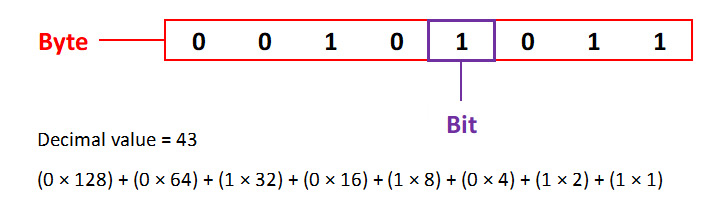
Quantifying bits and bytes
The word ‘network’ is widely associated with computing and data communication, though inherently the word comes from logistics. Now but especially before the Glass age, networks were applied for a variety of applications, and it’s these older applications that we still use to solve data communication problems. For instance, in the postal service, we use a unique hierarchical addressing system so we can forward on our mail through the relevant distribution channels. Reading up from the bottom of a letter to derive an address, postal code then house number/name. The same system is comparable to IP addressing, from left to right the octets identify the network then the host node dependant on the subnet mask or “class” of addressing you are using.
In the routable digital domain, each 32-bit address has four “octets” (also known as a ‘byte’) represented as an 8-bit binary numeral, each capable of representing 255 states. A network mask defines which bits of an address define the network portion and which is the node portion is (also known as a ‘host’). Because generally all nodes in a networks can see all packets transmitted by any other node on the network, we can apply subnet masking which separates the network and node addresses, turning big networks into multiple smaller networks, offering better local performance, organisation and security to the IT administrator.
Data on an IT type network is typically presented as a packet, transmitted from node to node, using a variety of transport protocols, the most common of which are TCP and UDP. Defined in layer 3 of the ISO model these protocols are responsible for encapsulation and routing between nodes. TCP is used by applications that require guaranteed delivery. It uses sequential acknowledgment windowing, incrementally increasing packet size until failure, before retransmitting at a lower rate. This provides fast, reliable data transfer that scales depending on adjacent traffic. (We see TCP for file transfer and the majority of web browsing.) UDP is used by applications that do not require the level of service of TCP, or that wish to use communications services not available from TCP. Applying in end-to-end communications, the packet is a fixed size, and if a segment is lost it is not retransmitted (we see UDP used for video streaming and digital audio communications).
AV technology using an IT infrastructure can demand a high load, with majority of users expecting a high resolution or bit rate of audio and video transmissions. Bandwidth capabilities are determined by the throughput of devices including routers, switches, and nodes on the network. As an audio like translation, this could be viewed as a threshold for network traffic. Without sufficient consideration for headroom, peaking will occur more frequently which leads to errors and ultimately lost data. Therefore, it is important to understand the potential load on a system, before applying your AVoIP technologies such as AES67 and SDVoE.

Why the twist?
Looking at high quality networked AV technologies, it is apparent that for the best service solution, we need to consider bandwidth. Therefore the transport medium needs to be capable of coping with the load presented returning minimal loss. In this case, by using the taxonomy “transport medium” I am referring to cable, termination and node computation elements, in other words the physical components of an IT type network. Every piece of equipment that supports IT networking will have an Ethernet data rate limit, defining the maximum bandwidth that the chipset in the product is able to support. With exponential hunger for faster data rates, in some instances this restriction can become the bottleneck in your network. Consequently the first step when finding an IT type solution, is to ensure that the product is rated higher than the expected load you intend to present.
Using IP transport standards to encode and decode information to and from the analogue domain via sampling, we can theoretically send more information down the same line, the caveat being the quality of reproduction. This is only possible in both the digital and analogue domain if we have consideration for the physical transport medium, Category (CAT) cable, post CAT 3, being the most widely adopted transport medium. In the analogue domain, we can utilise “QTP” and “Format A” type termination which uses the wiring convention with much the same functionality as a 4 pair multicore. In the digital network domain however, termination is typically an RJ45, conforming to ether EIA/TIA 568A or EIA/TIA 568B standards, with the latter being more prevalent. This standardisation presents interoperability for all components of an IT network.
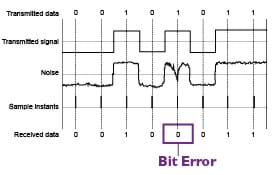
Errors primarily occur when there is interference on the transport line, inducing a change in binary state of the packet being transferred, resulting in this data being presented incorrectly to the receiver or switching node. Unfortunately, this occurrence is inevitable but manageable given the range of quality of service (QoS) available in modern products. QoS can be applied to retransmit & confirm packet information to ensure (as best as possible) that the data received is identical to that transmitted. We can also track the speed of which the information is transported in its complete form, logging transport latency and restrict traffic flow, hierarchically prioritising curtain packets above others. For instance, holding email traffic for retransmission, allowing telephone calls to use more of the networks throughput.
When we send data in a binary format we induce a pulse of electrical noise down the medium of choice, which creates a magnetic field, based on the frequency produced by the rate of throughput on the medium. By firstly shielding the cable with a ground we can reduce minor external radiation interference, as well as redirect any conducted voltage spikes away from sensitive equipment into the surrounding conductive encapsulation. The twist and shielding of modern day wiring, is a direct result of interpreted, harmonic, electromagnetic analysis, providing signal protection and noise cancellation through balanced signal lines, and utilising inverted phase. In a balanced line, each twisted pair of wires carries equal and opposite signals, the twist im-proves rejection of external interference. At the destination one signal is flipped, and the two are summed, nulling the difference (noise) between the two signals.
4k UHD @ 14 GB trunking
With 4K video rising in popularity, the demand for the ability to transport and even stream high resolution content is increasing. Although UHD resolutions compress down to a barely manageable 9.8 GB/sec, streaming true 4K would require bit rates of 14 GB/sec and upwards, requiring more throughput than domestic switches are currently capable of. For faster data rates past CAT 6, the application of Fibre is being widely adopted, although CAT 7 can theoretically support speeds up to 40 GB/sec, the bottleneck of this copper solution is the RJ45 termination, and associated product termination. D-link or GG45 connectors are currently the prominent way to utilise more of the capabilities of CAT 7 but dramatically reduce the viable distance between nodes.
Seemingly a simple answer, some switching products do implement trunking functionality, allowing users to increase the data rate of a transmission by coupling two or more ports together, on each end of the connection, offering an increase in speed at the cost of physical ports. With some forward thinking, this increase in the requirement may soon demand that switches become un-ideally single function, resulting in dedicated LANs for larger file types. Incorporating system performance enhancements on typical networks can be achieved through evaluation of network traffic and the implementation of VLANs, trunking and QoS analysis based hierarchical prioritisation. UHD and content buffering, masks the inefficiency of today’s networks from the demands of users, substantial adoption of newer technologies is the only way we will be able to support high resolution media going forward.